How It Works
The KeyCaliber platform consumes security logs from your EDR, vulnerability scanner, firewall, IAM, and other security products, selecting the data fields that are relevant for our AI/ML and analytics.
The logs are parsed to identify all assets (network addressable instances of compute).
Assets are correlated and de-duplicated so that each unique asset has an aggregated profile of details. Asset details are then featurized for AI/ML algorithms and transformed for additional types of asset behavior analytics.
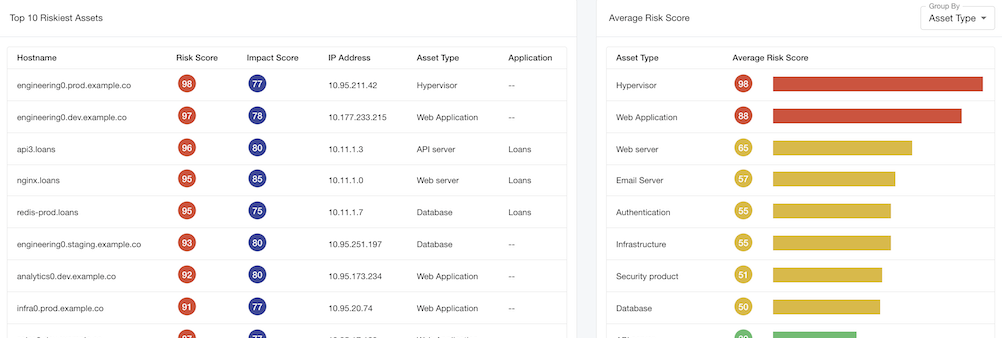
The full asset inventory is produced which includes the impact score, risk score, connections, and security coverage for each asset. With this information, the platform generates a ranked list of the most critical assets, most risky assets, most urgent vulnerabilities, and most serious alerts, presenting this data in dashboard and report form.
Connectors Include:
and more.
Finds every asset in the environment
Discover on-premises and cloud assets, information technology (IT) and operational technology (OT) assets, managed and unmanaged (Shadow IT) assets, by parsing security telemetry to show you what you have, where it is, and how it’s all connected.
Groups assets into business applications, and business applications into business processes to produce the MVC
Utilizes tags and additional fields to automatically group assets, and also applies AI/ML to infer which assets should be part of a business application when the tagging is missing or incomplete, to provide a full view of the minimum viable company (MVC).
Scores all assets based on their criticality to business operations
Computes a business impact score for asset using asset behavior analytics to determine the criticality of each asset and identify Crown Jewels.
Calculates the cyber risk of each asset, business application, and business process
Uses the asset impact score as well as all relevant data on vulnerabilities, exploitability, coverage gaps, adjacent risk, and more to provide a risk score for each asset and then aggregate the risk for business applications and processes
Ranks everything in priority order so you know what to secure first
Prioritizes vulnerabilities, alerts, and assets with coverage gaps so that your team can focus on what matters most to the organization and optimize limited resources. For MSSPs and MSPs with multi-tenant environments, ranking can be on a client basis and across the client base.
Shows security coverage gaps and overlaps
Determines which security tools are covering each asset. Your inventory view shows coverage gaps that need immediate resolution and coverage overlaps where you can reduce spending.
Visualizes potential attack pathways
Maps the connections between assets so you can understand attack pathways and dependencies.